Threat detection and response solutions
Protect your organization from the full range of cyber threats while drastically reducing internal effort. GLESEC provides an intelligent combination of industry-leading technologies and managed services that delivers the most comprehensive threat detection and response solutions at a fraction of the cost of building in-house.

Click image for more detail.
Adaptive, Cost-Effective Security for Your Needs and Environment
PROBLEM
Cybersecurity is tough (and expensive) Organizations face an ever-growing range of cyber threats, but only the largest organizations can afford to build and maintain a strong enough security posture to defend against them.
SOLUTION
Replace patchy internal controls with holistic, fully managed protection GLESEC combines industry-leading technologies with expert human analysis to deliver a consolidated, 24/7/365 managed threat detection and response solutions that covers all threats across your entire IT environment.
IMPACT
Build a world-class cybersecurity posture Our services allow any organization to benefit from the type of cybersecurity program only the largest global enterprises can afford - eliminating technology refresh costs for good.

Our threat detection and response solutions
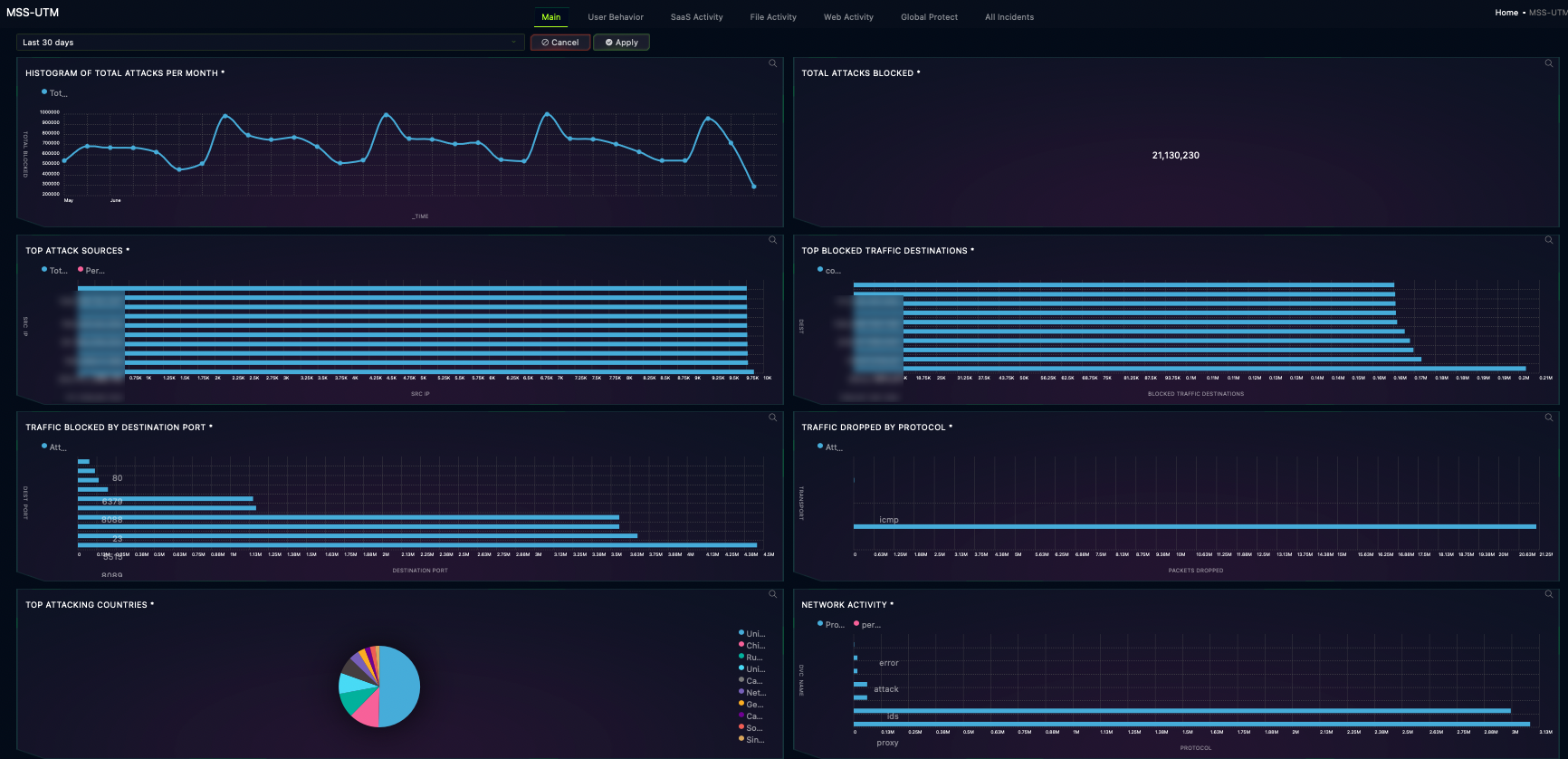
UTM Security
Protect your entire infrastructure, from on-premise to the cloud.
Today’s Next-Generation Firewall (NGFW) tools are powerful but come with a heavy manual burden of maintenance, management, and configuration. Our UTM service gives your organization the full protection of a modern NGFW, but with fully managed security policies, management, and reporting configuration, customization, and maintenance.
DDoS Protection
Denial of service attacks are frequently used to disrupt operations, damage infrastructure, and extort organizations into paying ransoms. Our managed DDoS Protection service provides complete, adaptive defense against the most advanced and high-volume attacks, protecting your organization from costly downtime.
Managed SOAR
Security automation promises a lot but rarely delivers because most organizations lack the skills and time to design, develop, and maintain automated playbooks.
This fully managed service pairs best-in-class SOAR technology with GLESEC’s decades of cybersecurity expertise to give your organization the true benefit of SOAR—without the significant internal effort required to develop and maintain it.
USB Management
USB drives are a common source of data loss. Protect your organization’s data with a combination of highly secure encrypted USB drives and a fully managed technology platform that makes it easy to remotely provision, secure, manage, and audit USB drives, ports, and virtual folders.
Endpoint Security
Protect your entire infrastructure, from on-premise to the cloud.
Today’s Next-Generation Firewall (NGFW) tools are powerful but come with a heavy manual burden of maintenance, management, and configuration. Our UTM service gives your organization the full protection of a modern NGFW, but with fully managed security policies, management, and reporting configuration, customization, and maintenance.
WAF
Protect your websites and web applications from cyberattacks, maximizing availability and user experience while preventing costly and damaging data breaches.
Web applications are a popular target for cybercriminals. Our fully managed WAF service defends against the full range of threats (including complete coverage of OWASP Top 10 attacks) with zero burden on your internal security team.
Data Loss Prevention (DLP)
Track and protect your sensitive data wherever it’s stored - in the cloud, on-premise, or even on a remote worker’s device. This fully managed service protects against malicious and accidental data loss, damage, or theft, including ransomware attacks. Easily meet data privacy and security regulations while protecting your organization against damaging and costly data breaches.
FAQs
FAQ's
You ask, we answer!
TECHNOLOGY PARTNERS
TOOLS BY THEMSELVES
DO NOT deliver A comprehensive threat detection and response solutions
Full Protection, Minimum Effort and Cost
Find out how your organization can dramatically enhance its cybersecurity posture while reducing internal effort and costs.