Security Testing and Validation Services
Find and fix gaps in your IT and security architecture
Proactively uncover and close weaknesses in your IT and security controls to reduce cyber risk and boost resilience to attacks. GLESEC provides comprehensive security assessments, pentests, and managed breach and attack simulations to ensure your architecture, applications, data, assets, and people remain safe and your organization meets regulatory and compliance requirements.
Click image for more detail.
Click image for more detail.
There’s More To Security Testing Than Pentests
PROBLEM
Misconfigurations and wrong tools cause breaches Many organizations unknowingly have vulnerabilities in their security posture and IT architecture caused by poorly chosen or configured security controls. This creates a false sense of security that is only dispelled when a serious breach occurs.
SOLUTION
Rigorous testing is the only way to uncover security gaps GLESEC provides an intelligent combination of security testing and validation of security controls to proactively uncover and resolve gaps before an attacker can exploit them.
IMPACT
Tighten your cybersecurity posture Proactively boost cyber resilience and build a realistic understanding of your organization’s cyber risk profile by systematically finding and closing vulnerabilities and security gaps.

Security Testing and Validation Services at a glance
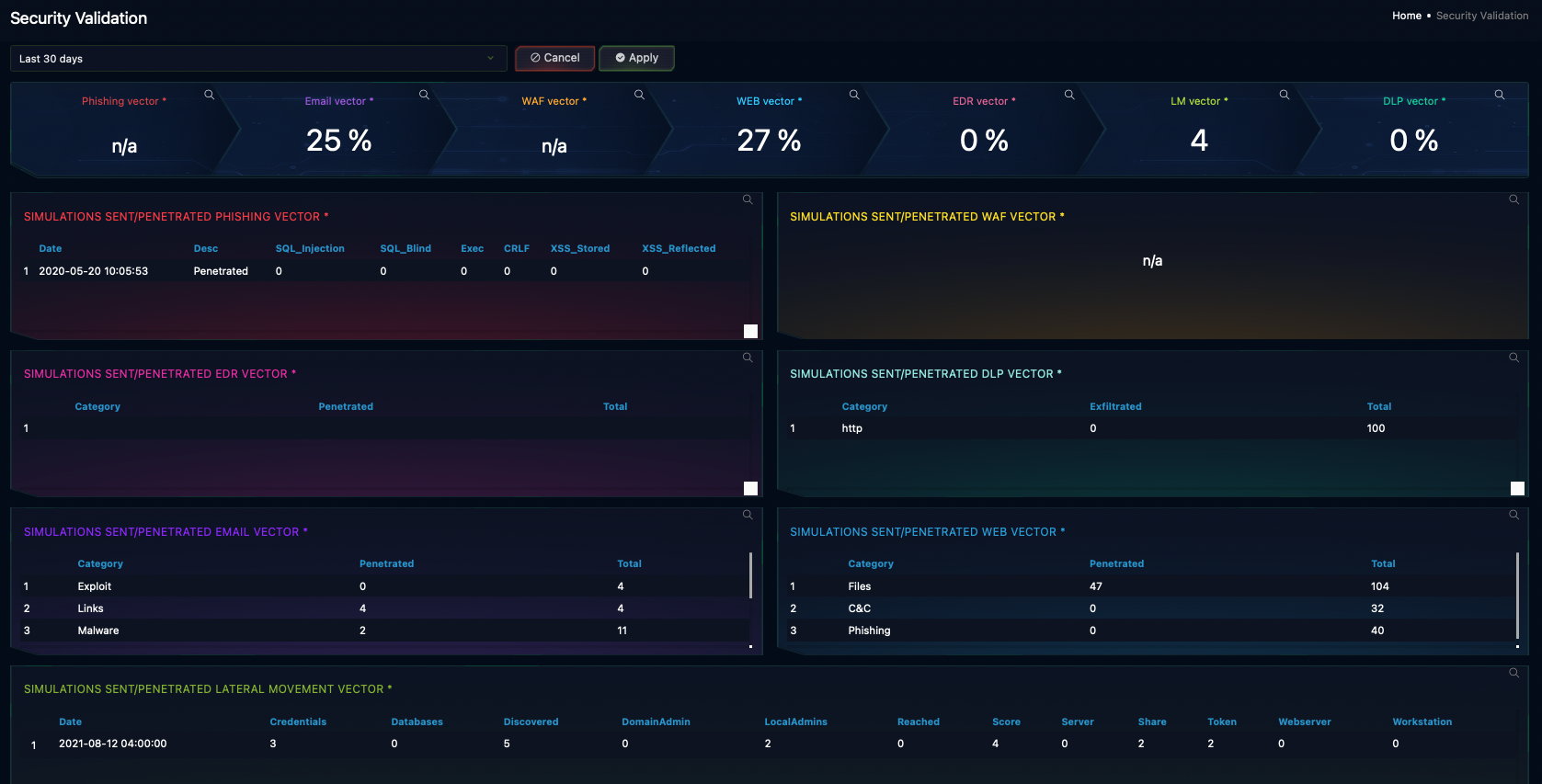
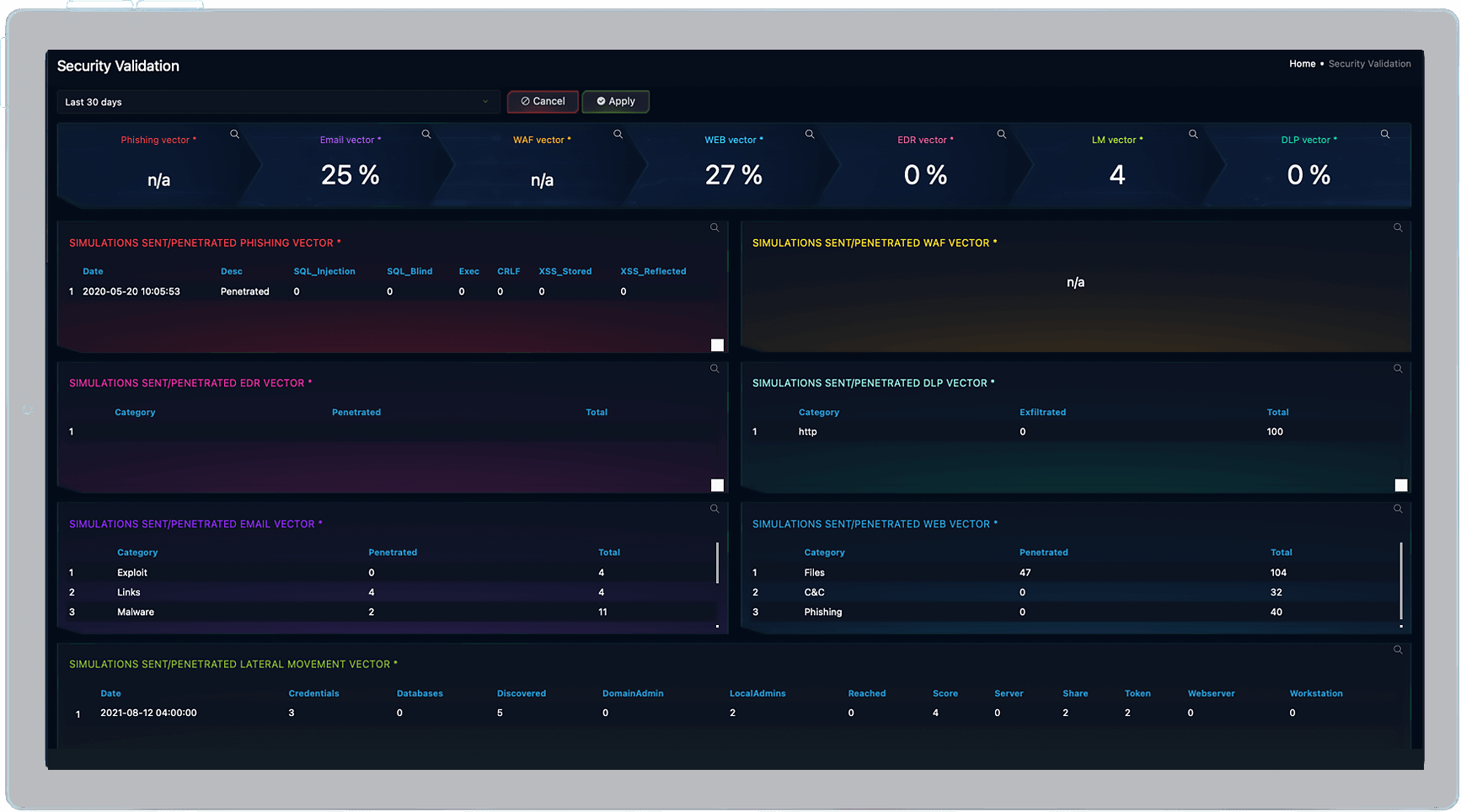
Breach and Attack Simulation
Poorly configured or ineffective controls create a false sense of security and leave your organization vulnerable to attack.
Our fully managed BAS service continuously validates the effectiveness of security tools like WAFs and uncovers gaps in your defenses. The service simulates real threats in your live environment for total accuracy with zero risk. Our experts guide you through corrective actions to resolve gaps and reduce cyber risk. The service covers:
- Email controls
- Browser controls
- WAF
- DLP tools
- EDR
- User awareness
- Lateral movement
- Immediate threats
FAQs
FAQ's

You ask, we answer!
TECHNOLOGY PARTNERS
TOOLS BY THEMSELVES
ARE NOT ENOUGH TO FIND AND FIX GAPS IN YOUR IT AND SECURITY ARCHITECTURE
Validate
Your IT and Cybersecurity Posture
Find out how GLESEC can help you uncover weaknesses and validate your cybersecurity controls.